Vulnerability Details
The vulnerability details table is a comprehensive resource that contains all known information about the selected vulnerability. This includes details about the nature of the vulnerability, any known exploits, and potential mitigation strategies. In addition, the table provides context for the vulnerability by listing any related vulnerabilities or known attack vectors. By presenting this information in a structured format, the vulnerability details table enables users to gain a deeper understanding of the threat landscape and make informed decisions about how to protect their systems.
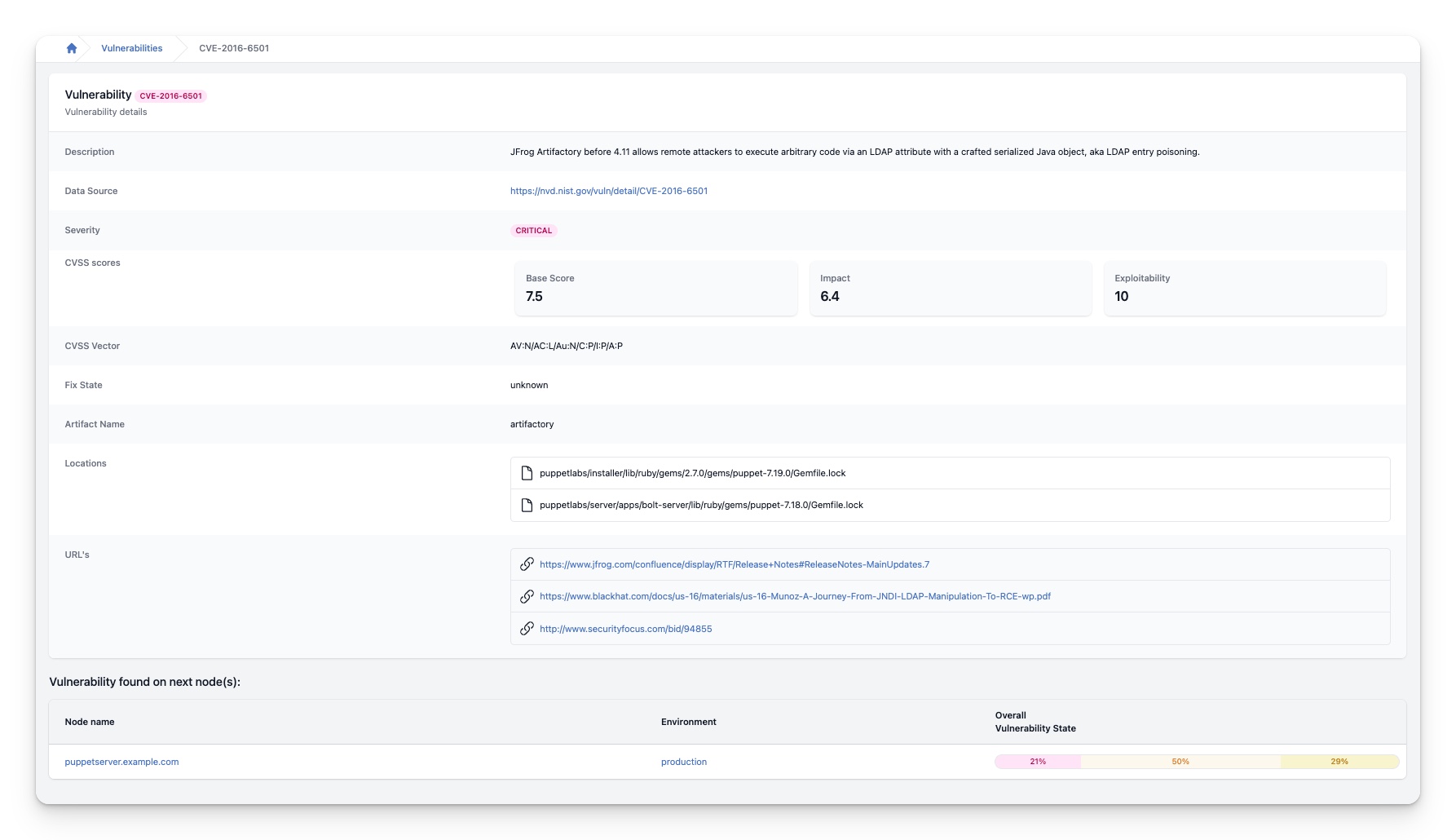
For the selected vulnerability, this information is shown:
| Item | Description |
|---|---|
| Description | A brief summary of the vulnerability in question. |
| Data Source | The source of the vulnerability. Refer to the list below for possible sources. |
| Severity | The level of severity of the vulnerability. For details on how severity is calculated, see the Common Vulnerability Scoring System version 3.1: Specification Document. |
| CVSS scores | The scores obtained using the Common Vulnerability Scoring System for the chosen vulnerability. See paragraph CVSS score below for more information. |
| CVSS Vector | The CVSS score can also be represented as a compressed vector string, which is a textual representation of the values used to calculate the score. For more information, see the Common Vulnerability Scoring System Version 3.0 Calculator. |
| Fix State | Indicates whether a solution is available for the selected vulnerability. |
| Artifact Name | The name of the artifact that contains the vulnerability. |
| Locations | The locations of the files that contain the vulnerability. |
| URLs | Links to resources where more information about the vulnerability can be found. |
Vulnerability Sources
When InControl performs a scan for vulnerabilities, it does so using a vulnerability database that’s stored on your local filesystem, which is constructed by pulling data from a variety of publicly available vulnerability data sources. These sources include:
- Alpine Linux SecDB
- Amazon Linux ALAS
- RedHat RHSAs
- Debian Linux CVE Tracker
- Github GHSAs
- National Vulnerability Database (NVD)
- Oracle Linux OVAL
- RedHat Linux Security Data
- Suse Linux OVAL
- Ubuntu Linux Security
By aggregating data from these sources, InControl is able to provide a comprehensive and up-to-date view of potential vulnerabilities in your system.
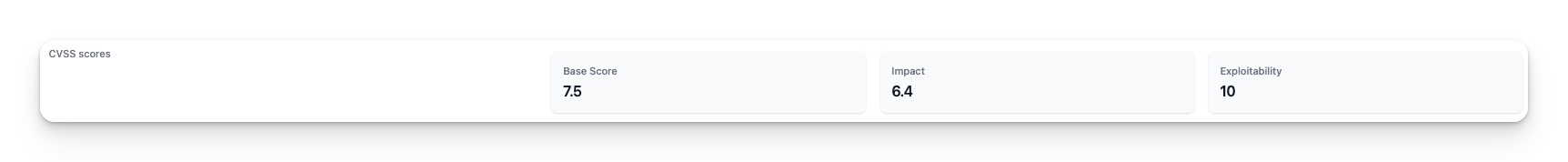
CVSS score
The Common Vulnerability Scoring System (CVSS) is a measure that aims to provide information on the characteristics and severity of software vulnerabilities in a way that is easily understood. The CVSS consists of several metric groups, and the Base metric group is especially important. This group represents the intrinsic characteristics of a vulnerability that remain constant over time and across user environments.
There are two sets of metrics in the Base metric group: the Exploitability metrics and the Impact metrics. The Exploitability metrics focus on the ease and technical means by which the vulnerability can be exploited. Essentially, they represent the characteristics of the vulnerable component or system. In contrast, the Impact metrics focus on the direct consequence of a successful exploit, and represent the consequences to the impacted component or system.
This means that when evaluating the severity of a vulnerability, it is important to take into account both the ease with which it can be exploited and the potential consequences of that exploitation. By taking a comprehensive approach that considers all relevant metrics, it is possible to develop a more complete understanding of the nature and risks associated with a given vulnerability.
See Common Vulnerability Scoring System version 3.1: Specification Document for the details of CVSS scoring.
Node table
The node table contails a list of all the node the selected vulnerability is detected on. The nodes table contains this information:
| Column | Description |
|---|---|
| Node name | The name of the node. Clicking the name will take you to the Node details page. |
| Environment | The number of nodes that belong to this Puppet environment. |
| Overall Vulnerability State | A small graphical overview of the vulnerability state of this node. |