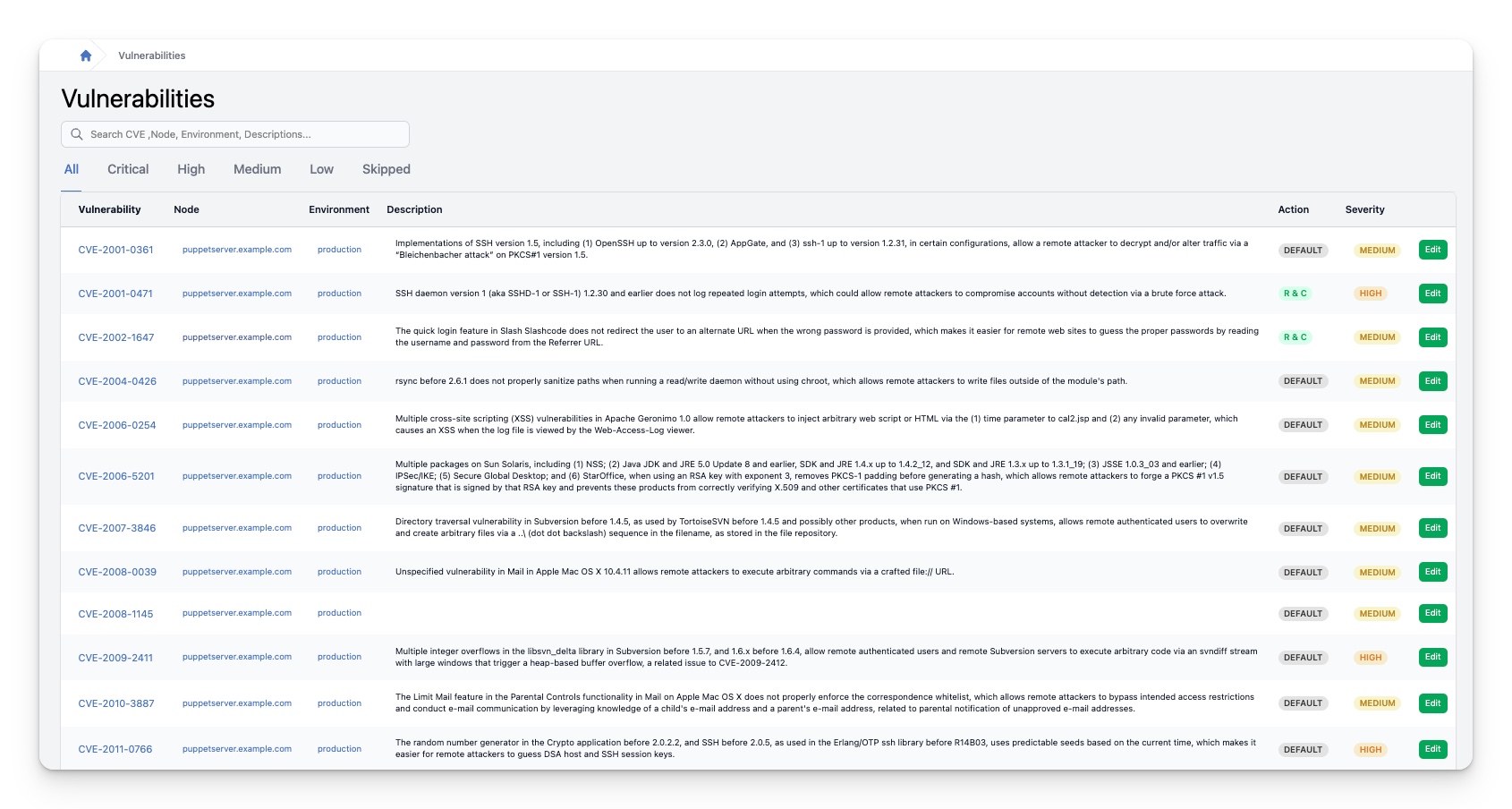
Vulnerability Occurrences
The “Vulnerabilities -> Occurrences” page is an important feature that allows users to easily view all detected vulnerabilities across all nodes. Users can navigate the page by selecting the corresponding tab, which displays vulnerabilities of a specific severity. In addition to the default “All” tab, several other tabs are available, including “Critical,” “High,” “Medium,” “Low,” and “Skipped.” This feature allows users to filter and view vulnerabilities based on their severity, which is particularly useful for those who need to focus on specific vulnerabilities or who want to get an overview of the severity of vulnerabilities across all nodes. Overall, the “Vulnerabilities -> Occurrences” section provides a comprehensive view of all detected vulnerabilities, making it an essential tool for any user looking to improve their system’s security.
Search field
When using CVE to search for vulnerabilities, there are several different ways you can approach the search. One way is to search by the node name, which can help you to identify vulnerabilities that are specific to certain components or areas of your system. Additionally, you can search by environment, which can help you to identify vulnerabilities that are specific to certain operating systems or platforms. Finally, you can search by description of the CVE, which can help you to identify vulnerabilities based on the types of issues they are known to cause. By using these different search methods, you can more effectively identify potential vulnerabilities and take proactive steps to address them before they can be exploited by attackers.
Vulnerability Table
The table contains the following columns:
| Column | Description |
|---|---|
| Vulnerability | This column shows the CVE number or another identifying number for the detected vulnerability. Clicking on it takes you to the Vulnerability details page |
| Node | This column displays the name of the node. Clicking on it takes you to the Node details page |
| Environment | This column displays the name of the Puppet environment where the node is running. Clicking on it takes you to the Environment details page |
| Description | This column provides a brief description of the vulnerability. If the column is empty, no short description is provided by the sources. |
| Action | This column displays the Puppet action for this vulnerability on this node. For more information, please see the explanation below the table. Clicking the “edit” button takes you to the Edit Vulnerability Occurrence form. Here you can change the action for this vulnerability on this node. |
| Severity | This column displays the severity of the detected vulnerability. |
Action
The action determines what Puppet will do with this compliance control. InControl offers the following:
- Puppet default
- Enforce only
- Validate only
- Validate & Enforce
- Skip